Rockets to Routers: The Cyber Dimension of the Israel-Hamas War
Technology is shaping the course of the war. As a range of actors involve themselves in the cyber domain, the likelihood of more widespread chaos increases.
In the midst of the kinetic warfare and traditional tactics evident in the 2023 Israel-Gaza conflict, a parallel narrative unfolds: the pivotal role of technology in shaping the course of the war. This article delves deep into this digital dimension, analyzing how cutting-edge technologies have molded strategic maneuverability, influenced battle outcomes, and subsequently rippled through the financial markets. While technology offers advanced capabilities, it also introduces a set of challenges and vulnerabilities.
Historical Context & Lessons from Past Conflicts
To understand the current conflict, it helps to look into its historical context. Israel's strategy in Gaza has never aimed at achieving a decisive, all-encompassing victory. While Israel has the military superiority over Hamas, a complete overthrow could pave the way for an even more radical group to take over Gaza. Moreover, Israel hadn’t wished to shoulder the burden of governing Gaza post-conflict. This led to Israel's “mow the grass” strategy - a periodic targeting of Palestinian militant leaders and high value targets to maintain manageable violence levels.
Most broadly, though, this is a story of deterrence. Israel never strived for a decisive victory in Gaza. While it could militarily defeat Hamas, Israel could not overthrow Hamas without risking the possibility that a more radical organization would govern Gaza. Nor did Israel want to be responsible for governing Gaza in a postconflict power vacuum. As such, Israel’s grand strategy became “mowing the grass”— accepting its inability to permanently solve the problem and instead repeatedly targeting leadership of Palestinian militant organizations to keep violence manageable. Rand, Lessons from Israel's Wars in Gaza
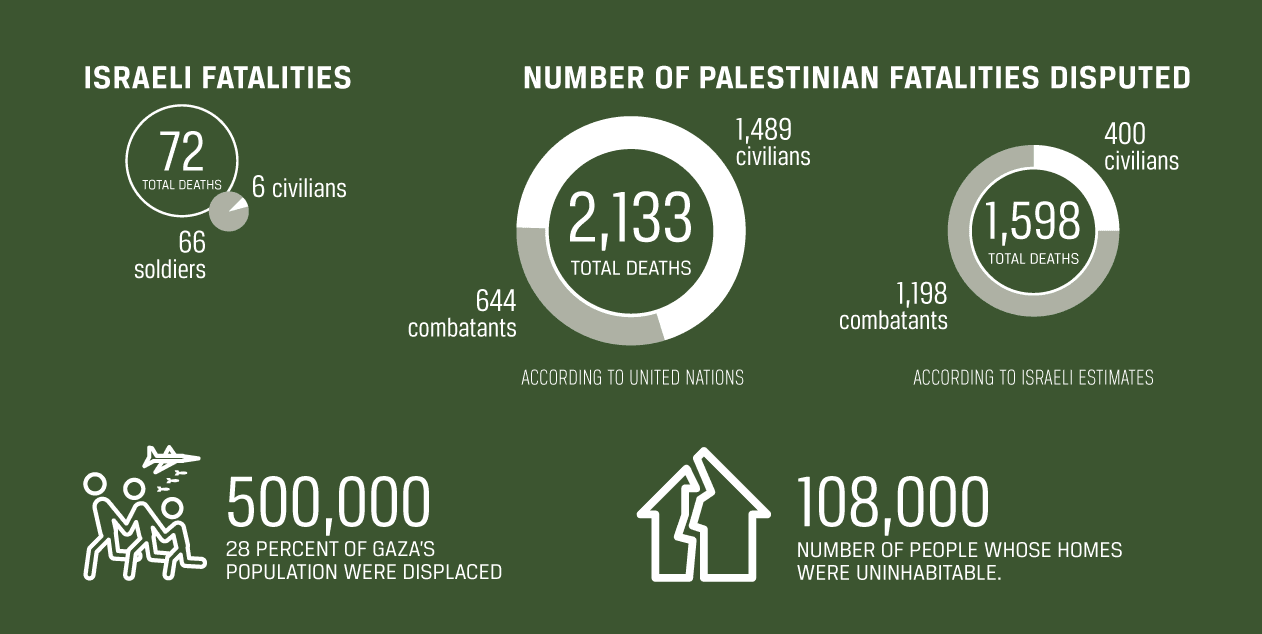
This approach was evident during "Operation Protective Edge" in 2014. A seven-week military campaign in response to rocket attacks from Gaza saw extensive airstrikes by the IDF and a ground operation targeting Hamas's tunnel network. The conflict led to the deaths of over 2,100 Palestinians and 72 Israelis. An Egyptian-mediated ceasefire marked its conclusion, but the operation underscored the fragile relationship between Israel and Palestine.
Beyond Deterrence: Israel's Empowered Position Against Hamas
“Iron Dome is a blessing because it buys Israel time, but Israel needs an excuse for why they are killing Palestinians in operations. . . . When Iron Dome works so well and so few Israelis die, Israel loses the justification for the operation” —Senior Israeli policymaker, Rand, Lessons from Israel's Wars in Gaza
The current conflict highlights the intertwined relationship between military technology and strategy. Israel's Iron Dome, for instance, has been a significant game-changer. Its efficiency, while shielding Israel against missile threats, has paradoxically reduced Israel's justification for operations due to decreased Israeli casualties.
Operation Protective Edge further exemplified the importance of technological advancements and their implications on warfare. During this operation, The Israeli Defense Forces (IDF) confronted the limitations of precision firepower, especially in dense urban terrains. The operation revealed that airpower alone couldn't achieve broader strategic goals, such as deterring Hamas.
Ground warfare insights from the operation also emphasized armored vehicles and Active Protective Systems (APS). Prior to the operation, Israel's defense investments leaned heavily towards intelligence and airpower, occasionally overlooking heavy armor's significance. However, post-operation assessments saw the IDF valuing APS more, not only for their protective abilities but also as strategic assets influencing battlefield decisions.
Before Protective Edge, the IDF invested in intelligence and airpower, often at the expense of particularly heavy armor platforms, while after it, the IDF is once again investing in armored vehicles. Active Protective Systems (APS) protected vehicles from rocket-propelled grenades and anti-tank guided munitions and had other indirect benefits on the battlefield, shifting the ways the commanders maneuvered and serving as an intelligence-gathering system. Rand, Lessons from Israel's Wars in Gaza
In sum, the conflict between Israel and Hamas underscores the balance between military technology and strategy. The introduction of advanced defense systems like the Iron Dome poses both opportunities and challenges, shaping the region's evolving geopolitics. And now with the loss of 1,300 Israeli lives and a newly reinforced fleet of armored vehicles, Israel stands stronger in its social credibility and hard power capability to dismantle Hamas.
THEREFORE, WHEN we think of the new Barak tank and the technology it has brought to the forefront, it’s worth considering it as part of this history. Wars and the kinds of weapon systems that are put into action are not fought in a vacuum. It is a common refrain that militaries learn to fight the last war, not the next one. In this case, Israel’s technology is trying to anticipate the next one. Jerusalem Post
Peace Illusion: Hamas Surprise Attack
In an unforeseen and meticulously orchestrated operation, Hamas stunned Israel with a surprise assault, reminiscent of the surprise that Egypt and Syria laid upon Israel during the Yom Kippur War 50 years prior. "Hamas employed a unique intelligence strategy that hoodwinked Israel over recent months," revealed an insider to Reuters. They created a public facade of reluctance towards confrontation while secretly preparing for this large-scale operation.
A False Dawn of Peace
The reluctance was evident when Hamas refrained from joining the smaller Islamic Jihad group in rocket attacks on Israel. This restraint was seemingly interpreted by Israeli leadership as Hamas's pivot towards prioritizing the well-being of Gazans over repetitive rocket attacks. In response to the perceived truce from Hamas, Israel reciprocated by permitting a growing number of Gazans to work within its borders, creating an illusion of a pathway to peace and prosperity.
Israel promptly reciprocated the de facto Hamas ceasefire by allowing thousands of Gazans to work in Israel—first 17,000, then 20,000, with the potential for many more. Their earnings were changing the lives of 100,000 family members with the possibility of even wider benefits. What was happening on the ground seemed to open a path toward tranquility for Israel and a degree of prosperity for Gaza.
Evidently it was all a delusion. Hamas, just like Arafat’s PLO, is willing to do everything for Palestine—and nothing at all for Palestinians. Edward Luttwak
The Shocking Assault
However, this apparent tranquility was shattered by Hamas's meticulously planned assault. Despite the hopes of burgeoning peace ties with other Arab nations and a potential deal with Saudi Arabia, Israel's political oversight of Hamas's intentions inadvertently lowered the nation's guard. Saturday’s assault laid bare Israel's security vulnerabilities. Hamas militants, with basic tools like bulldozers, and paragliders, breached Israel's billion-dollar security barrier on the Gaza border.
The Middle East Forum’s [Jonathan] Spyer called the attacks a failure of intelligence across the board, at both the strategic and technical level.
On the tactical level, Hamas “succeeded in knocking out the monitoring system at an early stage, using drones and weapons dropped from drones. There were facilities close to the border responsible for watching real time developments, and these were destroyed and disabled … I‘m sure there will be ways put in place to make sure that doesn’t happen again.” Breaking Defense
Additionally, a wave of rockets overwhelmed the famed Iron Dome missile defense system. Most alarmingly, Israel's elaborate surveillance apparatus – comprised of drones, cameras, and cyber tools – was rendered inefficient, as Hamas either bypassed or overloaded it. The aftermath had experts and citizens alike questioning the conspicuous absence of Israeli surveillance drones. As tech journalist Assaf Gilead stated somberly, the ones who were supposed to command those drones were no longer alive.
Rethinking Technological Dependence
While the immediate focus post-assault pivots towards repelling Hamas militants and rescuing hostages, the long-term view delves into the lessons derived from this attack. Was Israel's heavy reliance on technology its downfall? Some analysts contend that technology wasn't the primary issue. They emphasized a "failure of imagination" and an underestimation of the opponent.
Since Hamas took over as a governing faction in Gaza, Spyer said, Jerusalem has treated them as if they are more interested in ruling [Palestine] than in fighting Israel — an assessment that now appears to have been incorrect. Breaking Defense
As Israel reckons with the aftermath, the episode underscores the age-old lesson: while technological advancements are crucial, they cannot replace human vigilance, intuition, and understanding of ever-evolving geopolitical landscapes. It highlights the reality that risk of military surprise is likely to be an enduring factor in the 2020s, which is extremely consequential for global dynamics.
Bilal Saab, Senior Fellow and Director of the Defense and Security Program at the Middle East Institute, put it bluntly: “Over reliance on tech always has its drawbacks. But the problem here wasn’t tech. There was a failure of imagination, first and foremost, and total disrespect of the opponent.”
Similarly, Byron Callan, an analyst with Capital Alpha Partners, warned about jumping to conclusions about technology when people are involved.
“We don’t know if there was human intelligence warning of an impending attack, and warnings can be ambiguous. This doesn’t mean that technical surveillance in the form of space [and] air surveillance, signal intelligence, and cyber-network penetration has been devalued,” Callan wrote in a note to investors. “Rather, it again underscores the value of human sources and human assessments. It also means that the risk of military surprise is likely to be an enduring factor in the 2020s.” Breaking Defense
Cyber Attacks, an Increasing Role
Nation Security Agency senior cybersecurity advisor Rob Joyce explained yesterday [9th October] at a security conference in Sea Island, Georgia:
“One of the big worries, of course: is there a cyber component at this point? I’d say not yet.”
That being said, Joyce did acknowledge the U.S. had observed “small denial-of-service” attacks and warned that he expected “significant events” in the future.
Joyce isn’t alone in expecting the conflict to worsen, with Risk consulting, markets, and emerging business leader at PwC, Siddharth Vishwanath, also warning that the war is “Escalating in the physical world, and it is likely [to] escalate into a full-blown cyber warfare.” Technopedia
Recent developments in the Israel-Hamas conflict have highlighted the evolving landscape of cyber warfare. While traditional forms of warfare include land, sea, and air battles, the digital realm has now become a prominent battleground. The conflict has prompted nations and non-state actors to reassess their approaches to cyber threats, blurring the lines between physical and digital warfare.
The Israel-Hamas conflict serves as a stark reminder that the rules of engagement in cyberspace are still being written. The world is witnessing a paradigm shift in the way nations respond to cyber threats, blurring the boundaries between the digital and physical realms of warfare. The age of cyber warfare is upon us, and its implications for global stability are profound and complex.
Over the weekend, President Biden said he’d tasked his intelligence team “to make sure Israel has what it needs.” Matthew Olsen, assistant attorney general for the Justice Department’s national security division, confirmed at the conference that the US was working to understand if Iran played any part in the attack and whether Israeli and other intelligence had any inklings of the plans in advance.
So far, cyber operations themselves have played little role in the onslaught, said Rob Joyce, director of cybersecurity at the National Security Agency. At the conference, he cited only minor denial of service attacks and web defacements, but noted that this could change. “There will be others that pull into this fight. It just won’t be Hamas,” he said, without naming specific groups or countries.
Joyce said he also expected to see hacktivist action from unaffiliated hackers. While less technically sophisticated, they’ve still displayed a “very substantial capability” to threaten information flows, company finances and even critical infrastructure, he said. Bloomberg
Hard Power Response to Cyber Incursions: Israel's Changing Paradigm
In an evolving global landscape where warfare has expanded to cyberspace, the question of proportionate response to cyber threats becomes increasingly pressing. The Israeli military's airstrikes on 14th and 19th May 2021 against the supposed cyber bases of Hamas in Gaza highlighted a novel approach, marking a continued shift from soft power diplomacy to kinetic force in retaliation to cyber threats.
Crossing Cyber-Physical Boundaries: Israel's Paradigm Shift
Historically, states responded to cyber threats with soft power tactics, mainly including covert cyber offensives or diplomatic channels. The nature of cyber threats, being largely non-physical with few resulting in direct loss of life, led to this restrained approach. Israel's consecutive airstrikes against Hamas's cyber bases in 2019 and 2021 signifies a bold move away from this conventional wisdom.
While international laws governing cyber warfare are still in infancy, many states have benefited from the grey areas within cyberspace. This unrestricted freedom allows states to pursue foreign policy agendas covertly.
On the 14th and 19th of May 2021, the Israeli military conducted consecutive airstrikes against houses in the Gaza Strip that were allegedly home to Hamas cyber operations. The announcement came via the Israeli Airforce Twitter account, and closely mirrored the Israeli military’s bombing of Hamas cyber bases in 2019. Despite a two-year lapse between the attacks, Israel remains the only nation-state to have responded to cyber threats or cyber attacks through conventional military force. International concerns around the establishment of this precedent largely revolve around the perennial issue of how states can respond proportionately to cyberattacks. New Precedents in Cyberwarfare: Israel’s Airstrike of the Hamas Cyber Base, Bronte Munro
Cyber's Physical Manifestations: A Look at Stuxnet
The 2009 Stuxnet malware attack against Iran's nuclear facilities marked a significant shift in the cyber warfare landscape. What was primarily seen as a digital threat suddenly showcased its potential for tangible, physical destruction. Israel's airstrikes against Hamas further underscores the country's intent to blur lines between physical and digital realms, challenging the norms of cyber warfare.
Setting a Dangerous Precedent?
With over 50 significant state-related cyber incidents recorded in 2021, the normalization of kinetic responses to cyber threats could spell a volatile future for international relations. The risk of misguided retaliation, given the inherently challenging nature of attributing cyber attacks, increases the potential for widespread conflict.
Hamas's Cyber Operations: From Gaza to Turkey
Despite the constrained conditions within the Gaza Strip, Hamas's cyber activities persist. The group's cyber capabilities, while still in development, are not to be underestimated. Notably, Hamas's operations aren't restricted to Gaza. Being targets for the Israeli mow the grass strategy, Palestinian leadership has set up cyber operations in Turkey. The Turkish government, has provided a safe haven for Hamas leadership, potentially facilitating a base for planning cyber operations. Beyond Turkey, Hamas continues to receive support from Iran and Qatar, ensuring its cyber capabilities remain a threat in the region. This shift in cyber operations underscores the challenges of addressing digital threats through traditional force, as cyber initiatives are geographically unrestricted.
Hamas’s cyber capabilities, while relatively nascent and lacking the sophisticated tools of other hacking groups, should not be underestimated. It comes as a surprise to many security experts that Hamas—chronically plagued by electricity shortages in the Gaza Strip, with an average of just ten to twelve hours of electricity per day—even possesses cyber capabilities. Israel’s control over the telecommunications frequencies and infrastructure of the Gaza Strip raises further doubts about how Hamas could operate a cyber program. However, in 2019, Israel deemed the offensive cyber threat to be critical enough that after thwarting an operation, the IDF carried out a strike to destroy Hamas’s cyber headquarters, one of the first acknowledged kinetic operations by a military in response to a cyber operation. However, despite an IDF spokesperson’s claim that “Hamas no longer has cyber capabilities after our strike,” public reporting has highlighted various Hamas cyber operations in the ensuing months and years.
This dismissive attitude toward Hamas’s cyber threat also overlooks the group’s operations from outside the confines of the Gaza Strip. Turkish President Recep Tayyip Erdoğan and his AKP Party share ideological sympathies with Hamas and have extended citizenship to Hamas leadership. The group’s leaders have allegedly used Turkey as a base for planning attacks and even as a safe haven for an overseas cyber facility. Hamas maintains even more robust relationships with other state supporters, namely Iran and Qatar, which provide financing, safe havens, and weapons technology. With the assistance of state benefactors, Hamas will continue to develop offensive cyber and information capabilities that, if overlooked, could result in geopolitical consequences. The Cyber Strategy and Operations of Hamas, Atlantic Council
The Way Forward
As cyber threats persist and evolve, the international community faces a crossroads. On one hand, the unchecked potential of cyberspace offers countries opportunities to achieve foreign policy objectives covertly. On the other, the precedence set by kinetic responses to cyber threats threatens global stability. As more state and non-state actors delve into the realm of cyber warfare, establishing international norms and laws becomes imperative. Israel's approach, involving a mix of soft and hard power, offers a glimpse into the future of cyber warfare, one thing is clear: the age of cyber warfare is upon us, and the rules of engagement are still being written.
Cyber Aggression Against Israel in Current War
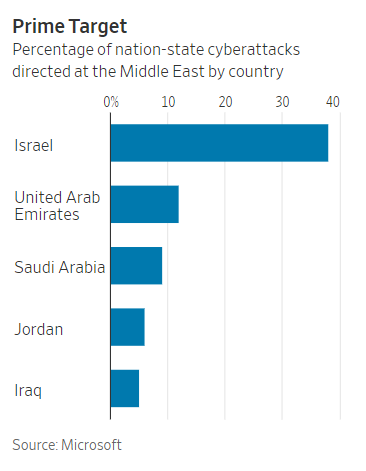
Israel stands as a hub for cybersecurity innovations, with its cybersecurity sector comprising over 400 international R&D centers and domestic companies that contribute over $3.5 billion in yearly exports. However, despite its prowess, the nation remains vulnerable to both cyberattacks and the spread of disinformation. Amid the intensifying conflict between Israel and Hamas, cyberattacks in Israel have surged. Key incidents include:
Billboard Hacks: Pro-Hamas messages and images were displayed on Israel’s smart billboards, as reported by Check Point Software Technologies.
Texts & Scams: Israelis received threatening texts and WhatsApp messages originating from Yemen and Afghanistan. Additionally, there were crypto scams masked as pro-Israel aid appeals.
Industrial System Attempts: There's been a spike in efforts to access Israel’s industrial systems, largely from Iran, Syria, and the pro-Russia hacktivist group Killnet. (These arracks are technically challenging and require sophistication).
Remote Learning Disruptions: A video of an armed man interrupted a high school video conference, prompting warnings from Israel's Ministry of Education.
DDoS Attacks: Many Israeli websites, including that of the Jerusalem Post, faced distributed denial-of-service attacks, causing temporary outages.
Critical Infrastructure Concerns: Experts fear more sophisticated attacks targeting critical infrastructure, potentially with assistance from Iranian hackers.
Disinformation: Examples include false claims about the compromise of Israeli water supplies.
Responses and Background Israel, being a prime target in Middle Eastern cyberattacks, has mobilized its tech community in response. Initiatives include:
Israel Tech Guard: A volunteer group from the tech community has been formed to assist in finding hostages and missing persons using online post clues, despite the distressing nature of some content.
Protection of Key Services: Volunteers are also bolstering security features for essential services, like missile-alert apps, and creating databases, websites, and apps for aid coordination and location services.
U.S. Support: The U.S. has promised "surging" cyber support for Israel, possibly in the form of communications links, replacement equipment, and crucial intelligence.
Who's Behind the Cyberattacks?
The recent cyberattacks targeting Israel emerge from a diverse set of actors, each with its own motivations and objectives. Here's a breakdown:
Hacktivists Seeking Notoriety or Pursuing Values: The group AnonGhost has taken a pro-Palestinian stance and is known for its DDoS attacks and attempts to target essential infrastructure and APIs. Most notably, they claimed responsibility for the alleged breach of the Israeli Red Alert missile warning platform. Hacktivism erupts in response to Hamas-Israel war, TechCrunch
State-Sponsored Actors: Iran, Russia, and China: While not explicitly mentioned, these nations have historically demonstrated advanced cyber capabilities and have been implicated in cyber offensives. The possibility of state-backed actors participating either directly or indirectly, by supporting other hacker groups, cannot be ruled out. Microsoft Digital Defense Report 2023
Organized Militant Groups: Hamas has been associated with cyber warfare efforts against Israel in the past. For instance, there have been allegations of Hamas disseminating malicious imposter versions of Israeli missile alert applications. The Cyber Strategy and Operations of Hamas, Atlantic Council
The cyber landscape in the Israel-Hamas conflict is multifaceted, with various actors playing roles driven by a combination of geopolitical objectives, ideological motivations, and the allure of chaos and notoriety. The amalgamation of independent hacktivists, state-sponsored actors, and organized militant groups creates a complex web of threats that Israel must navigate.
Hacking Palestinian Infrastructure
Various threat actors, both siding with Israel and taking a neutral or anti-Palestine stance, are emerging as key players in this digital warfare. While cyber elements are involved in disrupting Palestinian services, Israel’s kinetic warfare and control over Palestinian infrastructure are playing much larger roles in the current conflict.
Among the most notable actors is the Indian Cyber Force. The group have claimed to have successfully disrupted several websites. Among their targets are the Ministry of Transportation, governmental webmail services, the e-commerce platform U Buy, and the official Hamas website.
Meanwhile, the hacktivist group ThreatSec, which says it has “attacked Israel” previously, claimed it targeted Alfanet, an internet service provider based in the Gaza Strip. In a post on Telegram, the group claimed to have taken control of servers belonging to the company and impacted its TV station systems.
Doug Madory, director of internet analysis at monitoring firm Kentik, says that Alfanet was inaccessible for around 10 hours on Saturday, October 7—before the hacktivists posted their claim. The ISP’s systems have since been back online and communicating with the wider world. “Some of their services could still be broken,” Madory says, pointing to an Alfanet TV website and a web portal that were inaccessible on Sunday evening.
In response to a request for comment from WIRED via Facebook Messenger, Alfanet shared a statement in Arabic saying that communications were cut off due to “the complete destruction” of its headquarters. “Crews are working with all their might to restore service after the bombing of the headquarters and the main tower, despite the difficult and dangerous circumstances,” the message says via machine translation. The company did not comment on the role of a cyberattack, if any, in the outage. The Israel-Hamas war erupts in digital chaos
Cutting Off the Money to Hamas
Recent developments have put the spotlight on the role of cryptocurrencies in financing terrorist activities. While traditional funding mechanisms remain a significant source for Hamas, it seems that the flexibility, anonymity, and global reach of cryptocurrencies are presenting a new frontier for financing channels.
The Multi-Faceted Funding Machine
Researchers have pointed out that while cryptocurrency is a tool in Hamas's financial arsenal, it's by no means the only one. Traditional means like smuggling cash across the Gaza-Egypt border still remain in place. Moreover, Iran stands out as a stalwart supporter, with estimates suggesting Tehran channels around $100 million to the Hamas annually.
Iran already provides both Hamas and the Palestine Islamic Jihad (PIJ) with at least $100 million dollars a year, and it openly proclaims its intention to destroy Israel. Israel’s War on Hamas: What to Know, CFR
However, as Joby Carpenter, an expert on cryptocurrency and illicit finance at ACAMS, notes, “Crypto is another string in their bow.” Matthew Price, a former IRS investigator now with Elliptic, echoed this sentiment, stating that using crypto is “much easier than smuggling cash over Egypt’s border.”
The Challenges for Israel
Recent incidents have highlighted the difficulties both the U.S. and Israel face in cutting off foreign funding to these groups. PIJ and Hamas managed to amass significant weaponry and equipment, leading to the most notable breach of Israeli borders since the 1973 Yom Kippur War. The exact role of crypto in these operations remains uncertain. While significant funds were observed moving through digital wallets associated with these groups, the specific amounts seized by Israeli authorities and their exact use in operations are not yet known.
On Tuesday, Israeli police announced a move to freeze crypto accounts linked to Hamas. These accounts were allegedly used for soliciting donations on social networks. This is a part of a sustained effort to dismantle the “financial infrastructure in cryptocurrencies used by terror entities.”
The Mechanisms and Magnitudes
Cryptocurrencies operate by allowing users to instantly transfer tokens between digital wallets, usually held on a crypto exchange. This bypasses traditional banking mechanisms, and while it offers numerous benefits, it's this very feature that makes it attractive for illicit activities. Previous reports from the U.S. Treasury Department have highlighted this risk, citing instances where terror groups like the Islamic State and al Qaeda received donations via crypto.
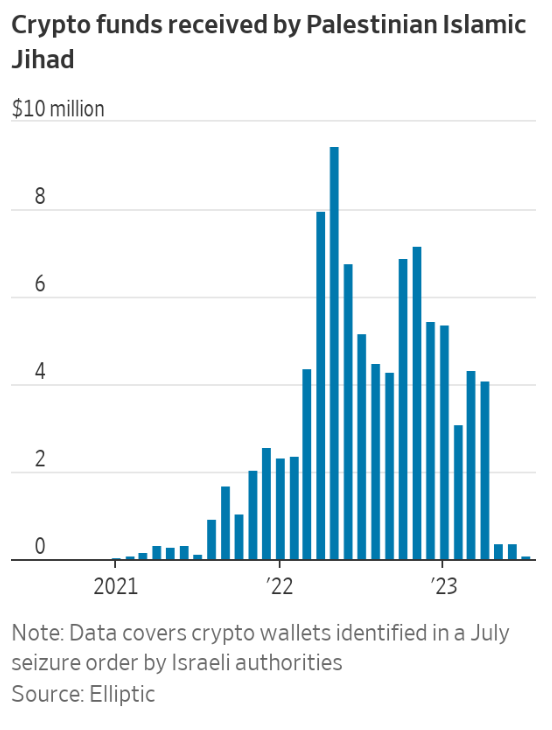
Recent data from Elliptic, a leading crypto research entity, reveals that digital wallets associated with PIJ received roughly $93 million in crypto between August 2021 and June the following year. In the same period, Hamas-related wallets garnered about $41 million, as per data from BitOK, a Tel Aviv-based crypto analytics firm. The charts below show the role of crypto in the Ukraine-Russia war for comparison.
Controversies Around Binance
Further complicating the picture is the role of established crypto platforms. Binance, a company founded in Shanghai and operating out of the Cayman Islands is one of the world's leading cryptocurrency exchanges. Binance was sued by the US Commodity Futures Trading Commission (CFTC) for various violations, including potential money laundering activities. Internal correspondences from Binance suggested a lenient stance towards suspicious transactions, even when linked to entities like Hamas.
In the evolving landscape of international finance and digital currencies, it's clear that regulators, governments, and crypto platforms have a shared responsibility. With terror entities seeking newer and more efficient ways to fund their operations, a multi-pronged and coordinated approach is essential to safeguard global security and economic integrity.
In March, the US Commodity Futures Trading Commission (CFTC) sued Binance for a series of violations. The lawsuit, one of many, even implied that Binance engaged in activity that could be perceived as criminal, including money laundering. Thus, for example, it was written that in February 2019, after the company received information about "Hamas transactions" on the platform, the head of compliance at the company, Samuel Lin, explained in an internal correspondence that "it's fine", terrorists usually send "small amounts" since "large amounts constitute money laundering", A colleague of his replied that he "could barely buy an AK47 (Kalashnikov assault rifle) with $600." Regarding other customers from Russia, Lin noted in another correspondence from February 2020 that "they are here for a crime” The Israeli police froze Hamas Cypto Accounts
Takeaways
The financing landscape of terrorist organizations is rapidly evolving, with cryptocurrencies emerging as a notable avenue for illicit fund transfers. This shift towards digital currencies, particularly due to their anonymity and ease of use, poses significant challenges for national and global security efforts. Regulatory bodies in the US are ramping up measures to exert control over domestic cryptocurrency exchanges and extend influence over foreign-based ones where feasible. In cases where direct oversight isn't possible, strategies like exclusion are could be considered. While cryptocurrencies like Bitcoin provide several legitimate utilities, their potential misuse cannot be overlooked. As a result, the global financial community should brace itself for heightened scrutiny and regulation in the crypto space.
Impact on Financial Markets
In recent days, as the geopolitical stage has seen a surge in hostilities, financial markets have been reacting with some very specific patterns.
Defense and Cybersecurity Stocks on the Rise
The axiom "buy the invasion" seems applicable, especially with defense stocks. Since last Friday, both Israeli and US cybersecurity stocks have seen an upward trend by 5-10%. Notably, US firms like Palantir and Crowdstrike and Israeli companies such as Checkpoint and Cyberark are part of this trend. The positive response, however, seems short-lived, with already visible signs of the growth plateauing. Additionally, the iShares US Aerospace & Defense ETF has climbed by 5% since the inception of the ongoing conflict. However, we caution against expecting this surge to sustain.
Our previous articles highlighted the escalating defense spending and its positive revenue implications for defense companies (see here). The rise in cyber breaches heightens the risk and public awareness of attacks, potentially boosting cybersecurity stock performance. Simultaneously, conflicts lead to increased usage of ammunition, benefiting defense manufacturers, especially those in the US. However, while this event is significant, it alone won't drive fundamental shifts in these sectors, barring wider conflict escalation. Instead, it complements a broader trend of increased defense spending and fits into the overarching macroeconomic context.
Oil Market in Flux
BCA's stance on petro-state instability outlines a complicated landscape. It indicates that both Russia and OPEC might curtail oil production, leading to a rebound in oil prices. Furthermore, the Saudis are unlikely to assist the Biden administration while the US-Iran engagement continues. This dynamic scenario, with Iran's oil production being the sole growth, indicates that a potential oil shock is looming, especially with Iran's nuclear program still active.
A reminder to everyone that Israel-Palestinian conflicts this century have not been market relevant. I am open minded that this can change, but thus far "what happens in the Levant, stays in the Levant" has been a reality. - Marko Papic
In a different part of the world, talks between Venezuela and the U.S. are progressing. The focus is on providing Caracas with sanctions relief by permitting foreign oil firms to take Venezuelan crude oil as debt repayment, conditional to resumed talks with opposition in Mexico. Earlier, there was a U.S. proposal to ease sanctions on Venezuela's oil sector, contingent upon the nation moving towards a free election.
In summary, the current global tensions have cast a complex and evolving shadow over the financial markets. With defense and cybersecurity stocks rising and the oil market navigating a web of geopolitical influences, stakeholders across the globe remain watchful and anticipatory.
Possible Conflict Expansion
In a rapidly digitized world, cyber threats are taking center stage in conflicts and political upheavals. The recent increase in cyber attacks related to Israel's situation and the Russia-Ukraine conflict has demonstrated how geopolitics now spill over into cyberspace, affecting not only governments but also major corporations.
Increasing Cyber Conflict: Impacts for Australian and New Zealand Organizations
Hamas-Israel Conflict and Its Implications for AUNZ Organizations
The recent escalation in the Hamas-Israel conflict has increased the potential for ideologically-motivated actors to target AUNZ organizations with DDoS attacks in the upcoming month. Over 30 groups ideologically aligned with various countries, including Russia, Ukraine, India, Pakistan, and Bangladesh, have redirected their social media channels towards the conflict. And over 70 DDoS attacks were reported against targets in various countries. Several points indicate a heightened risk for AUNZ organizations:
Association with sectors like financial services, energy and utilities, government, education, healthcare, media, and airports.
Presence in or partnerships with Israel or nearby regions.
Connections to political reactions to the conflict, e.g., think tanks, universities, or businesses where key members have public opinions about the situation.
Potential Threats to AUNZ Organizations
Pro-Russia hacktivist groups that previously targeted AUNZ may amplify their campaigns, exploiting the ongoing conflict.
DDoS remains the predominant mode of attack, but website defacement and hack-and-leak strategies might also be employed.
While AUNZ's condemnation of Hamas might place them in the crosshairs, there's a higher strategic priority for other regions at the moment.
Currently, there's a minimal chance that AUNZ entities will face destructive attacks linked to the conflict, but this can change rapidly.
Cyber Threat Landscape in Australia and New Zealand (AUNZ)
Recent analyst briefings have highlighted a growing concern regarding pro-Russian cyber groups, which are expected to intensify their cyber campaigns targeting Australia and New Zealand. This escalation is largely due to these nations' political stances and their public condemnations, such as that of Hamas.
CyberCX, a prominent cybersecurity firm, has flagged two particular groups as being especially active during the current conflict. These include one group responsible for a recent outage of Australia's Department of Home Affairs website and the pro-Russian Anonymous Sudan group, known for at least 24 DDoS attacks on Australian entities.
Record-Breaking DDoS Attacks
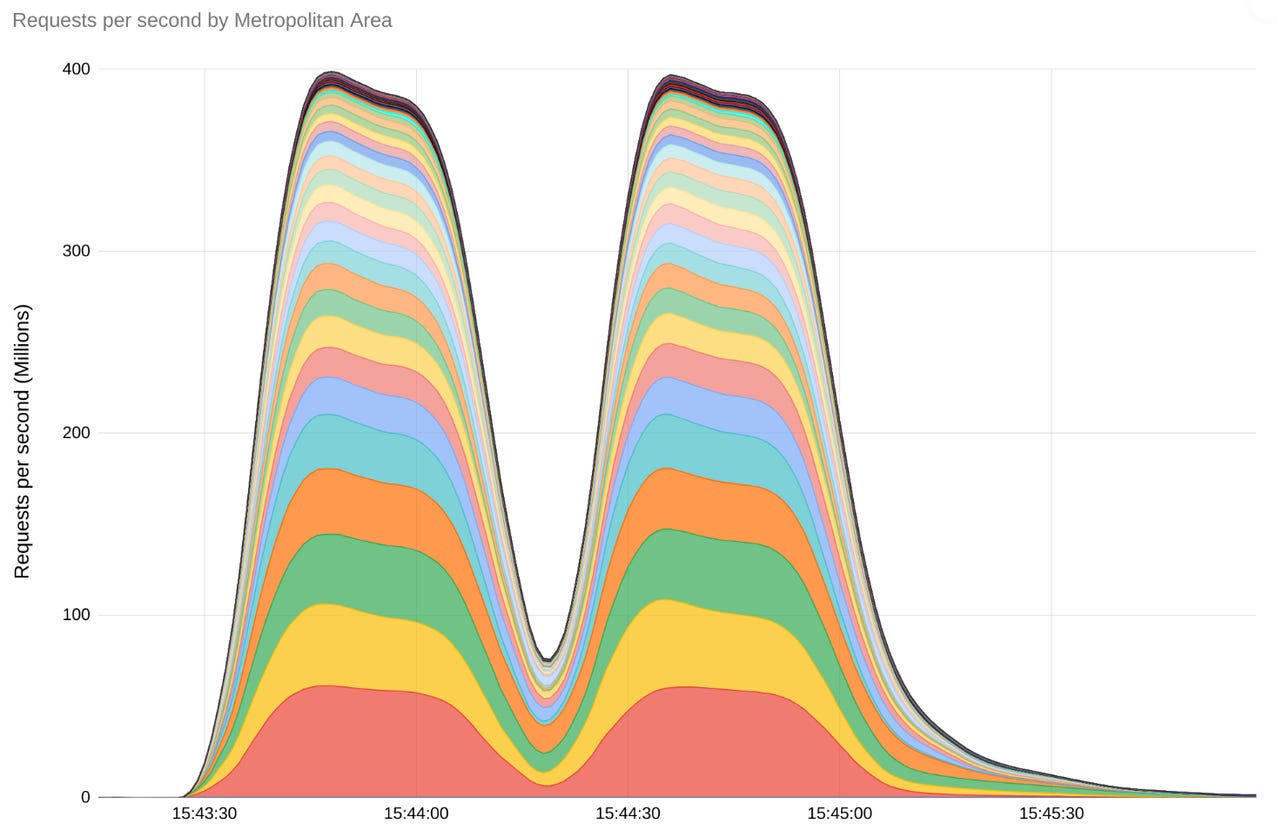
Despite being a relatively low-brow form of cyberattack, DDoS attacks are notorious for their potential to inflict significant harm. This was recently demonstrated when Google Cloud experienced a record-breaking DDoS assault in August. This attack, which peaked at an astounding 398 million requests per second (RPS), employed a novel "Rapid Reset" method. To put it into context, this attack was seven and a half times larger than any prior known DDoS attack, which had peaked at 46 million RPS in 2022.
Google wasn't the sole victim. Both Cloudflare, a top cloud delivery network, and Amazon Web Services (AWS) reported similar large-scale DDoS attacks, with RPS figures of 201 million and 155 million, respectively.
The Cyber Front of the Russia-Ukraine War
The conflict between Russia and Ukraine, which ignited in 2022, set a new precedent in terms of cyber warfare's role in military campaigns. CrowdStrike Intelligence has tracked a range of cyber activities linked to Russia throughout the conflict. These activities span from intelligence collection and attempts to sway public sentiment to deploying harmful attacks on government and commercial networks.
While Russia has been integrating cyber capabilities into its military strategies for years, often deploying DDoS attacks, the 2022 activities underscore the nation's willingness to employ a diverse set of tools in pursuing its objectives.
The intertwining of geopolitics and cyber warfare suggests that in modern conflict, the digital domain is critical. As nations and corporations continue to bolster their digital defenses, understanding these cyber threats is paramount.
Physical Element
In the volatile atmosphere of the Middle East, Israel finds itself navigating through an intricate maze of regional powers, each with its distinct stance and capabilities. While Israel faces resistance challenges within the confines of Gaza, another looming threat, Iran, takes center stage. The Iranian foreign minister's recent admonition for Israel to cease its offensive in Gaza is not to be taken lightly. Coupled with the caution of potential involvement from Hezbollah — which would inevitably spell catastrophe for Israel — this development is disconcerting. Particularly alarming is Iran's threats; its recent ascent to a de facto nuclear power status considerably broadens its strategic options and influence in the region.
However, it's noteworthy that Hezbollah's posture indicates a calculated restraint, at least for the time being. This restraint is attributed, in part, to the presence of U.S. military assets in the region. Although Hezbollah vocalizes its preparedness for confrontation, the organization has primarily called for reduced conflict. Yet, any action by Hezbollah, even if perceived as limited, holds the potential for unforeseen escalations. Misinterpretations and miscalculations could amplify the situation, especially if strikes inadvertently harm Israeli forces or civilians “The potential for miscalculation is exceptionally high.”
During the 2006 Lebanon War, Hezbollah had an arsenal of about 15,000 missiles, the most sophisticated provided by Iran and Syria, and wreaked havoc on the north of Israel. Today, Hezbollah has an arsenal of missiles believed to be ten times that, which are both more accurate and can travel greater distances. The entirety of Israel would then be vulnerable to missile attacks. Thus, there is every possibility of the war spreading, and the terrible bloodshed and tragedies (especially to the civilian populations) that will follow will make any kind of talks more fraught and more distant than in the past. In addition, Palestinian militants in the West Bank could rise up with violence at any moment, though this would be more likely if Israel were to launch a major ground attack and re-occupy Gaza. That would then raise the question: confronted by a three-front war, would Israel then target Iran in hopes of pressuring it to call off its minions? Israel’s War on Hamas: What to Know, CFR
BIS is Quiet on Chip Restrictions
Anticipation has been building regarding an imminent announcement from the U.S. Bureau of Industry and Security (BIS) on further China bans, which were hinted at last week for a release on October 7th. The recent developments in Israel have likely introduced an unexpected delay in this disclosure. The escalating situation in the Middle East might be diverting the attention of key decision-makers, thereby postponing other significant international policy announcements.
US Announces More Chip Bans This Week
US is Telegraphing Updated Export Controls Exclusive: US warned China to expect updated export curbs in October - Reuters The Commerce Department, which oversees export controls, is working on an update of export restrictions first released last year. The update seeks to limit access to more chipmaking tools in line with new Dutch and Japanese rules, othe…